>> Join the Tester Group << Request access to the private beta (approval is immediate)
>> Download on Google Play << Install the app and start testing immediately
Let me tell you something you already know: you reuse passwords. Maybe not everywhere, but definitely somewhere. You’ve got your “important stuff” password, your “who cares if this gets hacked” password, and maybe one or two variations in between. And when you do try to create a “secure” password? You write it down, save it in a notes app, or give up after the third password reset and go back to Summer2024!
I’m not judging you. I’m building for you.
The Problem: Security Theater vs. Actual Security
Every password generator in existence will spit out something like xK9#mL2$vQ7@wR4 and congratulate you on creating an “extremely secure password.” And they’re technically right–that password has high entropy, uses mixed case, includes numbers and symbols, and would take approximately 47 centuries to crack with brute force.
There’s just one tiny problem: you will never remember it.
Here’s what actually happens:
- You generate the perfect password
- You immediately forget it
- You write it down (defeating the purpose)
- Or you save it in your browser (potentially insecure)
- Or you click “forgot password” every single time
- Or–most likely–you just go back to using
Password123!everywhere
Microsoft’s 2016 Password Guidance found that password complexity requirements don’t actually improve security–they just make people write passwords down or reuse variations. The 2024 Verizon Data Breach Investigations Report found that 38% of breaches used compromised credentials, while research from Bitwarden shows that 85% of people worldwide reuse passwords across multiple sites–the #1 cause isn’t sophisticated hacking, it’s password reuse.
Here’s the uncomfortable truth nobody wants to say out loud: a “weak” password you actually use and remember is infinitely more secure than a “strong” password you can’t recall, reuse everywhere, or store insecurely.
The Memory Problem
Human memory isn’t built for random strings–it’s built for stories, emotions, and shocking content. Research shows we remember emotional, taboo, and humorous information far better than abstract data. This is why the XKCD “correct horse battery staple” approach works: random words create memorable stories.
But why use boring words when profanity burns itself into your memory through pure shock value?
Enter StrongAF Passwords
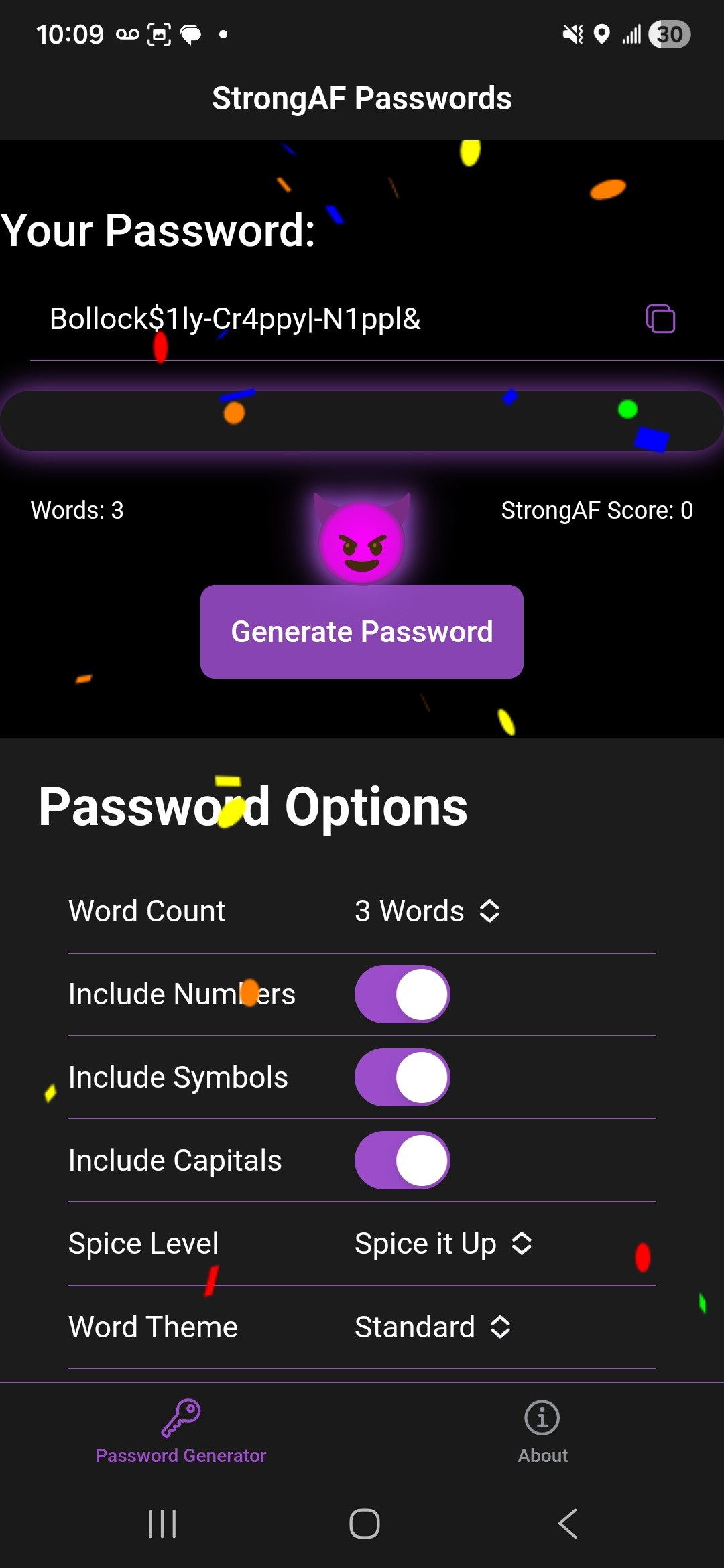
StrongAF Passwords is an Android app that generates high-entropy passphrases using curated dictionaries of funny, suggestive, and downright inappropriate language. The philosophy is simple: generate passwords that are both cryptographically strong AND actually memorable.
Get the App
Join the beta test and start generating memorable passwords today:
>> Join the Tester Group << Request access to the private beta (approval is immediate)
>> Download on Google Play << Install the app and start testing immediately
Limited to first 50 testers - Free lifetime access for all beta participants
How It Works
Hold-to-enhance generation: Select your word count, then press and hold the button. The longer you hold, the more character substitutions happen (a->4, e->3, o->0, s->5, etc.), replacing letters with numbers and symbols. Real-time feedback shows your security level ramping up.
Themed dictionaries with ~3,200 words:
- Standard: General profanity (“Keep it Clean” to “Trigger Warning”)
- Pirate: Nautical cursing (“barnacle” to “shitdeck”)
- Pitter-Patter: Canadian hockey slang for Letterkenny fans
- Drunken Bard: Medieval tavern debauchery for D&D players
Example: D1ck-Throbb1ng-Pounding-Rag1ngly-Tw@t-M@ssive (6 words, 48 characters)
Unlike xK9#mL2$vQ7@wR4, you’ll actually remember it.
The Security Math
Important: Entropy depends on HOW a password is generated, not what it looks like.
A password’s entropy is calculated based on the method used to create it. Standard password meters see “correcthorsebatterystaple” as 25 random lowercase letters (117 bits!), but that’s wrong–it’s actually 4 words selected from a 2,048-word dictionary, giving it only 44 bits. Security assumes an attacker knows your generation method (Kerckhoffs’s principle).
StrongAF: ~90 bits of entropy from:
- 3,200-word dictionary across 4 categories
- Specific word pattern (noun-adjective-verb-adverb-noun-adjective) = 3.1 x 10^17 base combinations (~58 bits)
- Character substitutions, symbol replacements, and delimiter variations (~32 bits)
- Total: ~90 bits
Comparison by generation method:
Password123!- Common pattern: ~28 bitscorrecthorsebatterystaple- 4 words from 2048-word list: 44 bitsxK9#mL2$vQ7@wR4- 15 random chars from 72-char set: ~95 bits- StrongAF 6-word - Pattern + transformations: ~90 bits
StrongAF achieves near-random password strength while remaining memorable. All generation happens locally on your device.
Is This For You?
Use it for: Personal email, social media, gaming, banking, password manager master passwords Don’t use it for: Work accounts, shared accounts, anywhere you’d need to say it out loud
Look–this isn’t for everyone. But this beats Password123!, beats reusing passwords, and beats writing them on sticky notes. Perfect security doesn’t exist. The best password is the one you’ll actually use.
If reading this made you think “wait, I’d actually remember that password”–that’s exactly the point.
Get the App
Ready to try it? Join the beta test now:
>> Join the Tester Group << Request access to the private beta (approval is immediate)
>> Download on Google Play << Install the app and start testing immediately
Limited to first 50 testers - Free lifetime access for all beta participants
Footnotes & References:
Microsoft Password Guidance (2016): https://www.microsoft.com/en-us/research/wp-content/uploads/2016/06/Microsoft_Password_Guidance-1.pdf
Bonneau, J., Herley, C., van Oorschot, P.C., & Stajano, F. (2012). “The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes.” IEEE Symposium on Security and Privacy. https://www.cl.cam.ac.uk/~fms27/papers/2012-BonneauHerOorSta-password--oakland.pdf
Shay, R., Komanduri, S., Durity, A.L., Huh, P.S., Mazurek, M.L., Segreti, S.M., Ur, B., Bauer, L., Christin, N., & Cranor, L.F. (2016). “Designing Password Policies for Strength and Usability.” ACM Transactions on Information and System Security, 18(4). https://users.ece.cmu.edu/~lbauer/papers/2016/tissec2016-password-policies.pdf
Verizon 2024 Data Breach Investigations Report: https://www.verizon.com/business/resources/reports/2024-dbir-data-breach-investigations-report.pdf
Bitwarden (2025). “Security habits around the world: A closer look at password statistics.” https://bitwarden.com/blog/a-closer-look-at-password-statistics/
Komanduri, S., Shay, R., Kelley, P.G., Mazurek, M.L., Bauer, L., Christin, N., Cranor, L.F., & Egelman, S. (2011). “Of Passwords and People: Measuring the Effect of Password-Composition Policies.” CHI Conference on Human Factors in Computing Systems. https://users.ece.cmu.edu/~lbauer/papers/2011/chi2011-passwords.pdf
NIST Special Publication 800-57 Part 1 Rev. 5 (2020). “Recommendation for Key Management: Part 1 - General.” https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-57pt1r5.pdf
Technical Note: All entropy calculations based on Shannon entropy formula with actual dictionary sizes from codebase. Character substitution probabilities calculated from replacement map frequency analysis.